An Incident Response Plan prepares an organization to deal with a security breach or cyber-attack. It defines the procedures an organization should follow if it discovers a possible cyber-attack, enabling it to detect, contain, and resolve problems promptly. Organizations need an IR Plan to safeguard their data, networks, and services from harmful activity and equip their staff to behave strategically. A robust IR strategy will assist businesses in detecting and responding rapidly to cyber risks, minimizing damage caused by such attacks, and ensuring the integrity of impacted systems. This article will cover incident response planning, cyberattack risks, the advantages of incident response planning, and its phases.
Risks associated with Cyber Attacks
Let’s take a look at some of the primary issues that cyberattack victims face:
Business Disruption
The early aftermath of a cyber attack may create major operational disruptions. Critical systems, for example, may become unavailable, interfering with production, sales, customer support, and other crucial tasks. It may lead to a breach of agreements or legislation. The issue is no longer merely an IT problem; it is a business issue, and CEOs are often called on to solve it.
Information Breaches and Data Loss
One of the most pressing problems after an attack is compromising sensitive data. The data may include consumer personal data (which may result in GDPR breaches) and sensitive company information and intellectual property. Breached data might be sold on the dark web or used for other harmful purposes. This raises the danger of a loss of trust, regulatory fines, a loss of competitive advantage, and even litigation.
Reputation Damage
The long-term damage to a company’s reputation may frequently outweigh the immediate financial impact of a cyber assault. Customers, partners, workers, and stakeholders may lose faith in a compromised firm. Sales may suffer, workers may leave, collaboration chances may be lost, or the stock price may fall. Finally, repairing this trust may require significant time and money.
Key Advantages of Incident Response Services
Incident response services provide various advantages that help companies react to and recover from security issues. These services contribute to event mitigation, fast reaction and recovery, evidence preservation, cybersecurity defense strengthening, and regulatory compliance. Businesses may improve their resistance to cyber attacks by harnessing the expertise of incident response service providers.
Here are some of the key benefits of Rapid Incident Response Services.
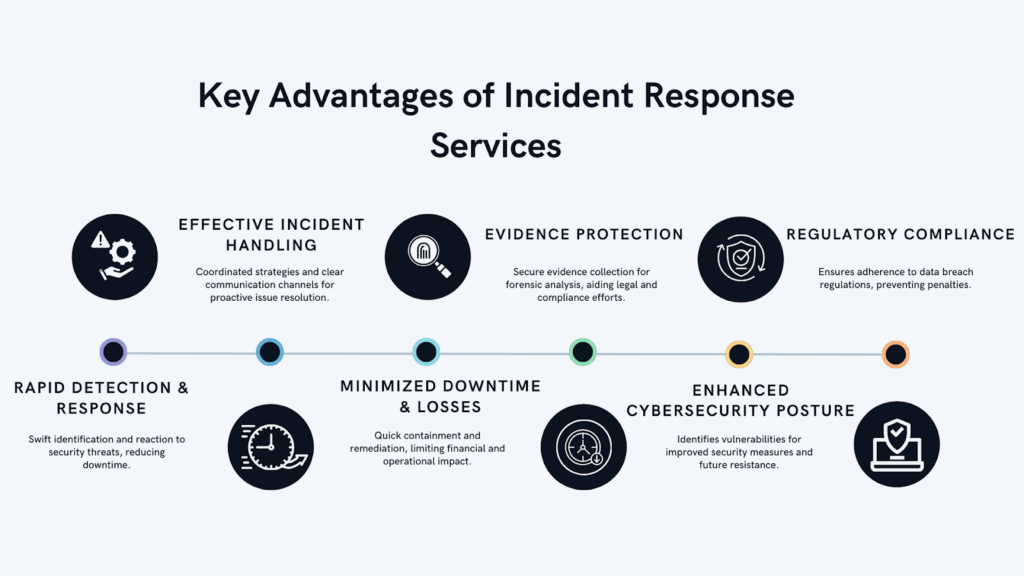
Rapid Detection and Response
A service for a rapid incident response can help organizations detect and respond to security threats quickly. Due to powerful threat intelligence technologies and continuous monitoring, these services can identify suspicious activity and possible breaches in real-time. An immediate response reduces downtime, decreases additional compromises, and lowers the firm’s overall impact.
Effective Incident Handling
An incident response service is more proactive than reactive, addressing security events before they occur and providing a method for planning and coordinating responses. They help businesses develop incident response strategies, define roles and responsibilities, and establish clear communications channels. The incident response teams are trained in implementing these plans effectively so they can reduce the incident’s impact and prevent it from escalating by guaranteeing a rapid incident response.
Minimized Downtime and Losses
A major advantage of incident response services is their ability to reduce downtime and financial losses caused by security issues. By quickly confining and resolving the issue, these services enable enterprises to quickly restore services. It reduces productivity, revenue production, and consumer trust, thus limiting financial losses.
Protection of Evidence
An incident response service plays a critical role in preserving evidence from security incidents. The evidence gathered can be used in forensic investigations, legal actions, and regulatory compliance. Using industry best practices and maintaining a chain of custody, incident response teams ensure that digital evidence is collected, stored, and recorded properly so that perpetrators can be identified and similar incidents can be prevented.
Enhanced Cybersecurity Posture
A company’s overall cybersecurity posture is improved by incident response services. The identification of vulnerabilities and weaknesses during incident response provides valuable insight into how to enhance security controls and take preventative measures. Lessons from the event response may be used to improve security methods, fix vulnerabilities, and increase overall resistance to future attacks. Preventive measures like using secure VPNs to strengthen network security can be incorporated into the lessons.
Regulatory Compliance
Many businesses are subject to stringent regulations governing incident response and data breaches. Event response services assist firms in complying with these standards by implementing a structured and documented strategy for event management. Businesses that engage with a reputed incident response service provider may guarantee that their incident response methods comply with regulatory requirements, avoiding fines and brand harm.
Phases of the Incident Response Lifecycle
The incident response life cycle is a critical mechanism that businesses use to manage and mitigate security issues successfully. According to the SANS Institute, it is broken down into the following essential stages:
- Preparation / Planning: During this stage, thorough incident management processes and tools are established. It comprises creating an incident response strategy, delegating roles and tasks, and establishing communication channels.
- Detection and Analysis: Organizations then work on determining and analyzing the nature of the occurrence. This involves monitoring security logs, doing forensic analysis, and gathering threat data to identify the breadth and severity of the event.
- Mitigation: Once an event has been identified and investigated, the next phase is to mitigate its effect and eradicate any dangers. This includes isolating vulnerable systems, fixing vulnerabilities, and deleting malware or unauthorized access points.
- Recovery: After the crisis has been mitigated, the recovery stage returns systems and operations to normal. This may include recovering data from backups, reconstructing damaged systems, and installing extra security measures.
- Post-event Activity (Lessons Learned): The last step is to analyze the event to learn from it and improve. This involves completing a post-event evaluation, recording lessons learned, and modifying incident response processes to handle future incidents better.
Conclusion
Rapid Incident Response helps the organization recover quickly and speedily from any potential attacks that may be affected. It identifies strategic activities, which include responses to breaches, containment of breaches, and promptly implementing remedial actions to protect sensitive data and prevent disruptions to business processes. This article has, therefore, delved into exploring the significance of incident response planning, highlighting the risks involved when it comes to cyber-attack incidences and highlighting the benefits of a responsive strategy.



