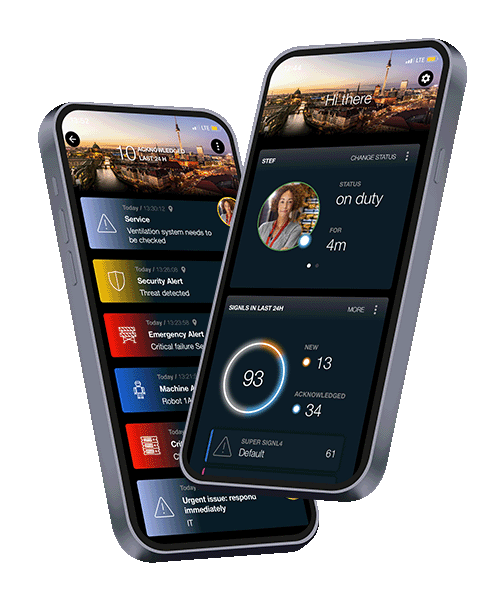
When critical Systems fail, don't hope for the best... respond 10x faster!
Stay ahead of critical incidents with SIGNL4 and its superpowers. SIGNL4 provides superior and automated mobile alerting, delivers alerts to the right people at the right time and empowers operations teams to respond and to manage incidents from anywhere.
Faster Incident Response
%
Less Unexpected Downtime
%
Less False Alerts
A proven solution
1000+ Customers worldwide

































iOS and Android App
Alerting and Incident Management. Anywhere.
SIGNL4’s advanced mobile alerting and incident management app serves as a unified command center for critical incidents and alerts from diverse systems and platforms. The SIGNL4 app transforms raw event data into actionable, context-rich alerts – featuring visual categorization, embedded links, location maps, images, videos, and more. It empowers response teams to act instantly, from anywhere.
Approved
SIGNL4 rates 4-5 stars in app stores and on review sites like Capterra & G2.





Ultra-Reliable, Instant Mobile Alerting
Automated Mobile Alerting
SIGNL4 delivers lightning-fast notifications via push, SMS, email, and voice – ensuring your team responds when it matters most. With intelligent time-based notification profiles, real-time delivery tracking, alert acknowledgments, and automated escalation workflows, SIGNL4 guarantees no alert goes unnoticed. SIGNL4 offers customizable push tones, mute override, and a rich set of mobile alerting features purpose-built for high-stakes environments.
Intelligent On-Call Scheduling and Shift Management
On-Call Management
SIGNL4 transforms how teams manage on-call duty with powerful, browser-based scheduling that eliminates the chaos of outdated spreadsheets. It ensures alerts are routed to the right people at exactly the right time, while a real-time dashboard provides instant visibility into who’s on duty – anywhere, anytime. SIGNL4 brings modern, on-call duty and shift orchestration to the frontline of critical operations.
Always connected, always responsive
After-Hours Call Routing
SIGNL4 redefines after-hours communication by delivering a powerful, enterprise-ready solution that ensures critical calls are never missed. SIGNL4 intelligently routes live voice calls to on-duty staff and seamlessly manages voicemails with instant alerting capabilities. With a single click, you can activate a dedicated inbound voice line across the U.S. and in over 20 countries.
AI-powered Alerting
AIOps
SIGNL4’s AIOps and AI Alerting features help IT and OT teams in mission-critical environments manage incidents more effectively than ever. From AI powered noise reduction and intelligent alert routing to AI-generated alert summaries, meaningful AIert Reports and even AI-assisted duty scheduling, SIGNL4 infuses artificial intelligence throughout the incident lifecycle to cut through noise and optimize response.

Seamless, Scalable Alerting Integrations
185+ Integrations
SIGNL4 connects virtually any system through email, webhooks, REST API, and advanced 2-way connectors. It consolidates events and alerts from diverse sources – spanning IT operations, IoT networks, industrial systems, and beyond – into a unified, actionable stream. With over 185 tested and verified integrations, SIGNL4 ensures rapid deployment, seamless compatibility, and enterprise-grade reliability.

“If you’re looking for a lightweight, effective way to manage operational alerts without overcomplicating things, SIGNL4 delivers. It’s easy to implement, highly reliable, and scalable as your use cases grow.”
“SIGNL4’s reliable alert notification system has eliminated manual processes, delivering instant cost savings and allowing our team to focus on what matters most.”
“It is a very nice cloud based tool with a lot of functions. Every alert can have its own category for a better overview. Excellent calender function. But the best is the easy to use app.”
Next Steps
Learn more about SIGNL4 and start your free 30-days trial of mobile alerting
What’s new: Insights and Use Cases
April 2025 Update – Fully Redesigned Signl-Center, Shift Tiers with Escalations, AI Shift and Duty Scheduling, and a new Chat View for the Mobile App
With our latest April update, we are setting a new benchmark in incident management excellence. The Signl-Center in our web portal has undergone a major redesign, delivering a superior, more intuitive layout, enhanced tracking of notifications and escalation...
AT&T Discontinues Email-to-Text Service: Why SIGNL4 is the Best Alternative
What Happened? In a move that has caught many businesses and IT teams off guard, AT&T has officially announced to discontinue its email-to-text gateway service. It is going to happen on June 17, 2025 (read more). This change means that sending text messages to...
Infrastructure Monitoring: A Comprehensive Guide to Integrating Effective Alerting
Imagine you’re the IT guardian of a busy company. Every day, you rely on infrastructure monitoring tools to keep an eye on your servers, networks, and applications. These tools are your early warning system – they spot glitches before they become full-blown problems. But what happens when an alert is missed or delayed? That’s where effective alerting comes in.
Certified Security
SIGNL4 protects your sensitive and confidential data! Derdack GmbH is a TISAX participant and meets the strictest criteria for information security and data protection.
Why SIGNL4?
SIGNL4 stands out as the ultimate solution for mobile alerting and team mobilization in the event of a critical incident, ensuring rapid response when it matters most. Unlike traditional notification systems, SIGNL4 offers automated, targeted, and persistent alerts that cut through the noise—reaching the right people at the right time via mobile push, SMS, and voice calls. With built-in alert filtering, duty scheduling, acknowledgment tracking, automated escalations, and seamless integrations with IT, IoT, and operational systems, SIGNL4 empowers teams to stay in control, minimize downtime, and enhance operational efficiency. Its intuitive interface, enterprise-grade security, and real-time collaboration features make it the go-to solution for businesses seeking reliable, fast, and actionable alerting and incident response wherever they are.




